Services
CONSULTING SERVICES
The need to remain connected to the outside world through technology is high for any organization. Nevertheless, it exposes them to cyberattacks which could put their integrity at risk. Organizations need to stay on top of their game and ensure their systems, structures, and practices can protect their assets from attack. Ultimately, product security directly impacts an organization’s cost and time-effectiveness. But beyond that, it is a make-or-break factor that affects the brand, its reputation, and public perception.
Approaching this issue might be complex and require specialized personnel.
Fortunately, SOTERIA Global’s consulting services will strengthen your security by providing you with guidance on how to protect your assets in the best way possible. Our hand-in-hand, customized approach will put you in touch with our in-house specialists who will lead you to choose the smartest, most efficient, and cost-effective security approach for your organization.
Solid, secured assets are the key to long-term success. We will be there for you along the way!
Approach us and we will work hand in hand with your company to safeguard your most valued assets and push you toward success!
- Threat Modeling and Secure Design
- Security Product Evaluations
- IP Protection
- Privacy and GRC
- Critical Infrastructure: Scada/ICS
Threat Modeling and Secure Design
As technologies play a leading role today, it is crucial for companies to step away from simply wondering about potential security threats. Instead, their approach must aim at implementing effective monitoring, detection, and mitigation processes to reduce risks and impact of attacks, and allow quick identification and response.
IT and Security teams should address two key aspects: i) what can potentially go wrong and ii) how effective the current measures are, if implemented. It is in this precise moment when threat modeling and secure design come to life. And this is particularly where us at SOTERIA Global will give you a helping hand.
SOTERIA Global’s specialized team of IT and cyber professionals will provide you the necessary guidelines and mentorship to effectively ‘model’ a structured threat detection process specifically tailored for your company’s needs. Our Threat Modeling and Secure Design consulting services will assist you in not only identifying threats but also prioritizing them based on their relevance and impact and, consequently, determining the most suited countermeasures and lines of action for mitigation.
Security Product Evaluations
Cybersecurity is a multilayered domain and the coverage of the in-house IT and Security teams can provide may turn rather limited at times. In this sense, focusing on the services and tasks your organization is specialized in and outsourcing those out of your core may be an efficient approach to respond to your cyber-related needs.
Outsourcing opens the door to a sizeable market of external solutions. Nonetheless, the roster of offers has expanded to an extent that choosing the ideal solution may be time consuming. Benchmarking entails not only expertise, but also, perhaps today’s most precious asset: time.
We at SOTERIA Global rely on broad expertise and the most qualified team of our in-house consultants to provide our clients with the top-notch product benchmarking mentorship and consulting, ensuring that our clients make the ideal selection of solutions to secure their data and assets to maintain resilient and well performing systems. With our help, you will be able to choose the best IT/Cyber solutions for your company.
IP Protection
Intellectual property is prone to being attacked from both internal and external actors. Organizations must identify those places that hold critical information, ensure they have secure and resilient data architecture, and monitor assets to guarantee these are not compromised. Mapping sensitive assets and designing information flow, architecture and procedures are a key to ensure minimum risk to intellectual property. Therefore, companies must perform a series of activities to guarantee the internal management structures as well as the security systems in the company protect its intellectual property from harm coming from any direction.
Detecting the pertinent loopholes in the structure and designing an adequate protection system for IP is a thorough process. To help organizations with the task, SOTERIA Global has rolled out its IP Protection consulting service. Our team of professional in-house experts will support you in safeguarding the integrity of your proprietary products and content. Our team will also mentor the organization in implementing continuous monitoring processes and best practices.
Privacy and GRC
Businesses require governance, risk, and compliance (GRC) to align to guarantee the security for their data and, moreover, their assets. And how are these elements rooted together? Data has steadily risen to become a pillar for organizations. As a result, these companies must implement new regulations and protection frameworks to ensure data will be, in fact, secured and kept private, and that any potential factor that might risk its safety is controlled. Subsequently, companies must comply to these regulations and frameworks accordingly. The fact that information technology is now being included within regulatory frameworks pushes IT teams further into delving into these and ensuring their works sets the ground for synching all these elements.
The rise of IT requires coordination to guarantee the security and integrity of data
Alignment might be a comprehensive task which requires skills and expertise. Our consulting solutions at SOTERIA Global will help you approach this task with absolute success. Our in-house IT and cyber specialists will give you a helping hand in defining your alignment strategy, based on the characteristics and conditions of your organization, and walk you along the way the processes of compliance and implementations of this strategies. We will ensure, through our consulting, your company gears toward effectively mitigating risks surrounding data integrity and privacy by ensuring the risk and compliance frameworks in place are the appropriate ones and that these are being put into action effectively.
What do we offer?
Critical Infrastructure: Scada/ICS
Implementing Supervisory Control and Data Acquisition (SCADA) and Industrial Control Systems (ICS) to automate the manufacturing processes and data collection is widely popular across a wide range of industries. Control systems directly work on organizations’ infrastructures to ensure their optimal operations. Therefore, penetrating an organization by blading these components has become a common practice by cyber attackers, as they disrupt operations directly targeting the organization’s infrastructure. This makes it imperative for organizations to actively look forward to implementing solutions to secure these components proactively and effectively from potential attacks.
Fortunately, our team of specialized professionals in the IT and Cyber field have carefully crafted SOTERIA Global’s Critical Infrastructure – SCADA/ICS program, particularly targeted at organizations looking forward to strengthen their capabilities and effectively safeguard these components. We work hand in hand with our clients to provide them with the best guidance in terms of risk management, security framework development, threat detection, and response planning among other relevant touchpoints, all aimed at protecting the integrity of the SCADA/ICS environments. Our consulting services will guide you to close your organization’s security gaps and ensure secure and successful operations.
PENETRATION TESTING SERVICES
As most operations within an organization today are significantly dependent on the well-being of IT systems, it is crucial for these to count of solid security controls. Determining how effective these are is key to find points of improvement and make tweaks to better protect your assets. As a result, thoroughly testing your entities’ security systems periodically must become a must in their agendas.
Penetration Testing both measures the degree of quality of their security systems and detects your organizations’ particular vulnerabilities. Outsourcing pen testing services to expert companies to effectively seal your business’ gaps and successfully manage risks is an investment that pays off.
We apply the following pen-testing methods to guarantee the most accurate results:
SOTERIA Global counts different testing modalities, allowing our testers to dissect and moreover dig deeper into different aspects of the systems, and furthermore, providing a more accurate and thorough assessment of your organization’s potential vulnerabilities.
BLACK-BOX
Black Box:
Black box testing treats the software without any knowledge of internal implementation. Black box testing can be regarded as an opaque and closed box. “Opaque” means we know nothing about its inside, and “closed” means we do not have the access to modify the source codes. Black box aims at examining the functionality of an application without diving into its internal structure.
GREY-BOX
Grey Box:
Grey box testing is the combination of black box testing and white box testing, aiming at identifying defects due to wronged structure or application use. It can be regarded as a clear and closed box because a tester know the details in the codes but do not have the access to change them. It takes the straightforward technique of black-box testing and combines it with the code-targeted systems in white-box testing.
WHITE-BOX
White Box:
As the tester performs White Box testing, they have access to the internal data structures, algorithms and codes. The tester can not only see the source codes but also manipulate the codes as part of testing process.
SOTERIA Global counts on top-notch expertise and to perform penetration testing on a broad range of areas within the IT spectrum
You will be provided with a complete view and thorough reporting on your organizations’ vulnerabilities with detailed insight on security threats and how to prioritize remediation and closure of existing gaps within your system. Assessing risks and threats before breaches actually take place will also help you avoid financial distress. SOTERIA Global will take the lead and guide you away from these drawbacks.
SECURITY PROGRAMS
Diving into the world of cyber brings along innumerable benefits, but also exposure to a full range of risks. Finding the perfect balance between these two elements, through the implementation of adequate systems and strategies must be a mantra for companies nowadays. However, tackling this balance is complex. Managing all the cyber-related services in-house is not always resource effective; outsourcing them to specialized organizations may be the most suitable option in order to optimally fulfil your cyber-security needs. This is the core motivation of SOTERIA Global: providing top-notch services to our clients, so that securing your most valued assets.
Our team of in-house experts will provide you full security services of the highest standards in the market. Our programs are based on best practices and are aligned with cost-effectiveness and the latest technologies in the industry.
Our team of in-house experts will provide you full security services of the highest standards in the market. Our programs are based on best practices and are aligned with cost-effectiveness and the latest technologies in the industry.
Approach us and we will work hand in hand with your company to safeguard your most valued assets and push you toward success!
Secure SDLC Process
When it comes to software development, integrating security testing and other related activities into this stage is crucial. Otherwise, the software would be an open door for exploitable vulnerabilities, potential attacks, and security incidents. Ultimately, this scenario would put businesses in danger and its assets in risk. Security must be applied at every phase of the Software Development Life Cycle (SLDC), so that threats are identified and dealt with before they end up taking a toll on the final products and potentially reducing the added value new features may bring. Besides, identifying threats or bugs during design and development io far less costly and time than during implementation.
Implementing secured SDLC processes properly is multi-staged, and each stage has specific components which require the working hand and mentorship of specialized professionals. Understanding that the process might be complex and tangled, we count on highly qualified, in house specialists and methods and the latest technologies to successfully implement the program. SOTERIA Global will further offer continued monitoring to ensure the software delivered complies to all the security measures and standards, translating to successful deliveries.
Vulnerability Management
Due to the open exposure to a growing number of cyber threats, Vulnerability Management has become a must for organizations; in fact, several compliance, audit, and risk frameworks already require its implementation. Given the fast-paced dynamics of the cyber environment, companies need to assess and take action on new information on a recurrent basis to proactively catch on vulnerabilities and shut the doors for potential incoming attacks. As a result, implementing an ideal Vulnerability Management program would effectively help you safeguard your organization’s assets by shrinking the possibilities of being potentially harmed by attacks.
We at SOTERIA Global understand how vital, yet complex and time-consuming, it is for our clients to secure their assets from the innumerable attacks they may be exposed to on a daily basis. This why we provide our high-end, end-to-end services and develop a tailor-made, effective program for you.
Through our Vulnerability Management Services, SOTERIA Global will thoroughly scan your environment in order to identify the risks your IT and network structures may encounter. From that point onwards, we will design and implement the Vulnerability Management program that better suits your conditions, and further define mitigation strategies. We will continuously monitor your vulnerabilities until their closure and will cyclically review the status of your company.
Approach us and we will ensure your company’s assets are secured.
Handling Insider Threat
Implementing strong and resilient cyber security frameworks and strategies entails defending an organization’s most vital assets from potential outside attacks. Nonetheless, it is crucial for IT and cyber security teams to consider that threats are not only external; attacks can happen from within. Internal threats might be perceived sometimes as less common but overlooking them is a tremendous mistake. Companies may be subject of theft, unauthorized access violations, unsafe practices, or accidental issues, all these happening among its members. Therefore, a global and resilient security framework is only complete when it considers and is ready to act against these internal threats.
To effectively respond to this context, SOTERIA Global has crafted a full, thorough program to help your organization properly identify the internal threats that may pertain its profile. The program, led by our team of top-notch in-house experts, is specialized in identifying and recognizing threat agents from within the company by analyzing particular behavior patterns or motivations. SOTERIA Global’s solution will provide hardening and thorough testing of your internal environment in order to ensure your assets are safeguarded from the in-house dynamics within your organization. Furthermore, we will guide the organization to promote best practices and further foster a culture of cybersecurity within its teams.
FORENSIC SERVICES
Understanding that the cyber threats organizations and systems face are numerous and can pertain any stage and aspect of their structure, SOTERIA Global also offers additional proactive and reactive forensic services. If your organization is victim of any sort of cyberattack, SOTERIA Global will take the lead in dissecting it, understanding its source, identifying recovery potential, and furthermore providing with strong insight on prevention strategies and actions. Our team of specialists has designed them to adapt to your organization’s circumstances, requirements and needs. If your organization has shown an incident, you SOTERIA Global will come and take over the challenge.
SOTERIA Global’s proactive and reactive services can be particularly tailored to your companies needs.
REMOTE / ON PREMISE
PERIODIC / SPECIFIC
3rd PARTY PRODUCTS & SERVICES
REMOTE / ON PREMISE
PERIODIC / SPECIFIC
3rd PARTY PRODUCTS & SERVICES
Take a look at our list of proactive and reactive services!
Proactive
Forensics
Web
Forensics
Reactive
Forensics
Incident
Response
Malware
Detection
SOC AS A SERVICE
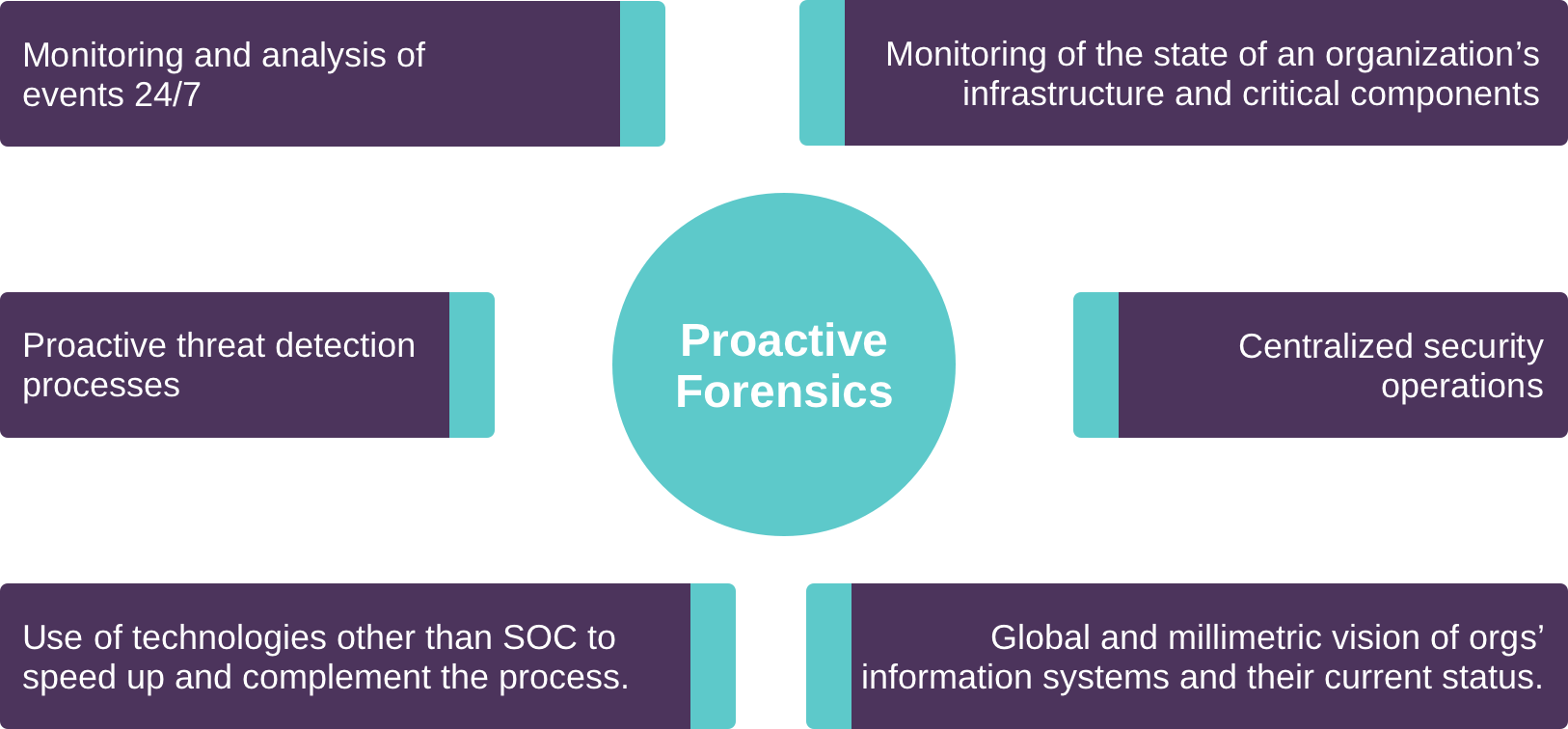
SOTERIA Global’s SOC Support Service as is network to help professionals dedicated to data protection by monitoring and reporting the state of their organizations’ systems continuously: 24 h a day, and 7 days a week, all year long. SOCs detect and prevent cyber threats from harming an organization’s system through tailored processes and technology. With SOCs, organizations seek to speed up their attack detection and mitigation processes. Nonetheless, running SOCs efficiently is a meticulous and somewhat complex task, requiring investment in money, skills, and time, one of today’s most treasured assets.
Considering the level of complexity behind SOCs, SOTERIA Global has carefully crafted a high-end SOC service. Backed by a team of top-notch, in house specialists, our service is guaranteed to speedily and timely identify, analyze, and treat cyber-related incidents. We will boost your organization’s threat detection and management abilities to heights, and more importantly, protect your backbone assets. We offer a customizable solution of the highest quality in order to adjust to our clients’ most specific needs. SOTERIA Global is the ideal partner and will drive your company to success!
Our SOC Support Service includes:
SOTERIA Global’s detailed pen tests for Internal and External Networks look forward to detecting weak spots which may put personal and financial information at risk in order to seal the existing gaps and further voiding potential threats. While internal network pen testing helps measure how much an attacker can achieve once they accessed the network, external testing evaluates perimeter security and identifies weaknesses in web, mail and FTP servers.
As Web Applications are highly prone to undergo cyber incidents, thorough testing on their frameworks, APIs, or coding are vital in order to evaluate to what degree these are secure. Our pen testing services will ensure the risks these are exposed to are mitigated.
SOTERIA Global’s Cloud Pen Testing will lead to finding weaknesses withing a system hosted on a cloud provider. The testing will provide you with a better understanding of the status of your cloud, reporting on any misconfiguration and advice on how to better secure your cloud systems.
SOTERIA Global’s pen tests for mobile application cover a wide range of aspects of it, including mobile platform internals, app development lifecycles, reverse engineering and tampering, software protection, session management, access controls, cryptography, error handling and data protection, among other key factors.
Effectively securing your network is key to safeguard an organization’s vital assets. These must be equipped with controls in order to detect and mitigate malicious moves or potential threats. Therefore, SOTERIA Global’s services cover pen tests for a vast range of areas withing the Network Security field, ranging from wireless networks to maintenance processes.
SOTERIA Global’s Secure Code Reviews will allow us to identify security-related weaknesses of an application’s source code. The reviews will provide developers insight on reshaping the source code in order to make it more secure.
Web Application Firewalls act as safety nets, offering protection from attacks against vulnerable web apps, and are key to secure a companies’ web environment. Performing evasion techniques On WAFs will allow the identification of loopholes in the firewall and lead to design better WAF strategies.
SOTERIA Global’s pen tests on ERP Systems are geared towards locating security gaps and issues coming from misconfigurations, default installations, and other sources. Security configurations of ERP systems are usually left to default, which may lead to potential weaknesses and exposure to vulnerabilities. Pen testing will allow to discover and strengthen these systems’ security configurations.
SOTERIA Global’s pen tests on ERP Systems are geared towards locating security gaps and issues coming from misconfigurations, default installations, and other sources. Security configurations of ERP systems are usually left to default, which may lead to potential weaknesses and exposure to vulnerabilities. Pen testing will allow to discover and strengthen these systems’ security configurations.
SOTERIA Global’s pen tests on ERP Systems are geared towards locating security gaps and issues coming from misconfigurations, default installations, and other sources. Security configurations of ERP systems are usually left to default, which may lead to potential weaknesses and exposure to vulnerabilities. Pen testing will allow to discover and strengthen these systems’ security configurations.
SOTERIA Global’s pen tests on ERP Systems are geared towards locating security gaps and issues coming from misconfigurations, default installations, and other sources. Security configurations of ERP systems are usually left to default, which may lead to potential weaknesses and exposure to vulnerabilities. Pen testing will allow to discover and strengthen these systems’ security configurations.
SOTERIA Global’s pen tests on ERP Systems are geared towards locating security gaps and issues coming from misconfigurations, default installations, and other sources. Security configurations of ERP systems are usually left to default, which may lead to potential weaknesses and exposure to vulnerabilities. Pen testing will allow to discover and strengthen these systems’ security configurations.
SOTERIA Global’s pen tests on ERP Systems are geared towards locating security gaps and issues coming from misconfigurations, default installations, and other sources. Security configurations of ERP systems are usually left to default, which may lead to potential weaknesses and exposure to vulnerabilities. Pen testing will allow to discover and strengthen these systems’ security configurations.
